Introduction
iViZ is the industry’s first company to position themselves as an on-demand
penetration testing service for web applications. This is very different from the normal low cost
vulnerability assessment services like
Qualys,
Hackersafe,
Hackerguardian etc. Unlike conventional solutions, iViZ delivers
consultant-grade quality with an on-demand experience. iViZ provides a hybrid solution that integrates automation with manual testing by security experts. This results in a cost-effective SaaS model to achieve a very low rate of false positives, manual expert validation, and business logic testing. The key advantages are high quality, on-demand manageability, high scalability and unmatched service to price value.
iViZ Security is funded by
IDG Ventures which also funded companies like Netscape, Baidu, MySpace and F5 amongst several others. iViZ currently has 200+ customers across several verticals including Finance, Telecom, Online Media and E-commerce.
Why did we evaluate iViZ On Demand Penetration Testing?
Although there are tons of
penetration testing providers and solutions in the market today, iViZ visualized the gap in making penetration testing more proactive and repetitive in a cost effective manner. It has thus adopted the SaaS route which can be a potential disruptor to make penetration testing more affordable without the hassles of tools and costly consultants. Organizations worldwide are evolving at a rapid pace and thus they require a solution which helps them attain speed to market and profitability.
Also today’s market place is primarily focused on cost differentiation. This has led to automation and sub optimal quality with plenty of “me too” service providers. While automated scanning provides benefits like lowered cost and faster time to scan,
application penetration testing requires manual intervention to remove false positives and more importantly conduct business logic testing. iViZ seems to have understood early on that pure automation will never be able to indentify complex business logic
vulnerabilities in the context of today’s evolving application specially in online and telecom market.
Review Parameters
We evaluated iViZ primarily on 4 key parameters:
- User Experience
- Quality of Findings
- Methodology
- Packaging and Pricing
A. User Experience
We had been provided access to
https://edge.ivizsecurity.com/ . The portal enables two views: partner and customer. The partner view essentially helps you manage your customer’s pen test. The customer can also login with his credentials and submit a new scan or download a complete report.
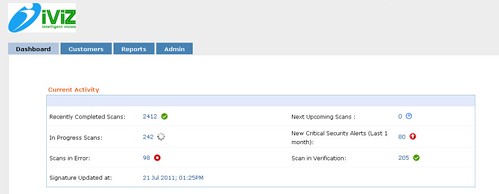
The dashboard nicely summarizes the essential info on completed scans and upcoming scans. “Scan in Verification” are the ones which have already passed automated testing and being manually verified for false positives and business logic testing. This hybrid testing is carried out by combining automation of testing with work flow automation and leveraging process engineering on top of it.
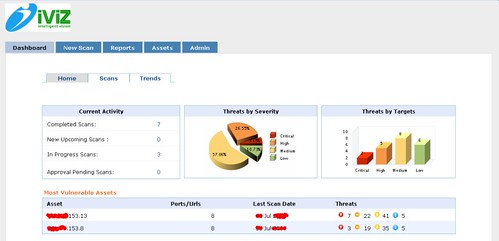
The customer dashboard is also clear and concise representing only the vital information without too much clutter of graphs and diagrams.
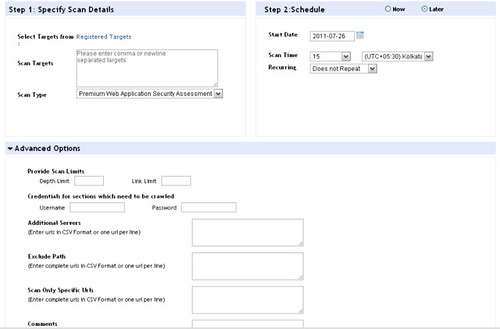
The interface to submit or schedule new scans has got plenty of options to specify advanced parameters that enhance the quality and performance of testing. Apart from date, time and target you can specify application details like user credentials, path to exclude, depth limit and link limit.
B. Quality of Findings
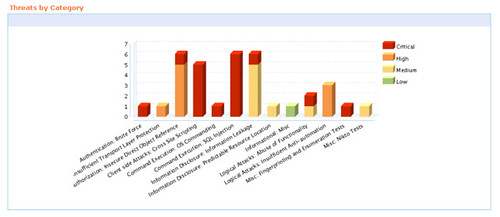
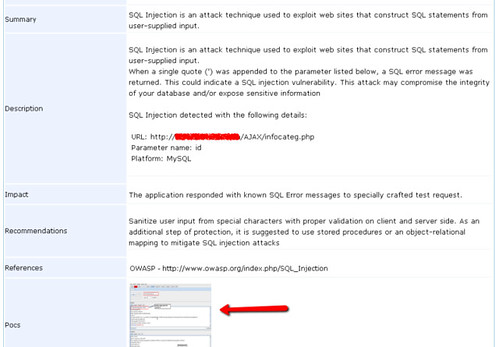
The key factor which differentiates this SaaS offering for other VA services is the quality of findings. The report section nicely summarizes vulnerability info and critical threats that needs to be fixed urgently. The reports can be viewed online or downloaded in a pdf format. The key thing which has impressed us is every high and critical vulnerability is accompanied by a
“Proof of Exploit” – a screenshot depicting the impact of the vulnerability. This goes a long way in making the report meaningful and immense help for the application developers to quickly fix the vulnerability. This also gives the true essence of penetration testing.
Having a proof of exploit with high and critical vulnerability also ensures that these have been manually verified and thus the report is almost “Zero False Positive”. A huge time saver!
C. Scan Methodology
iViZ Penetration Testing Cloud service jumpstarts the scan process without employing consultants or buying expensive tools. Assessments are conducted in the cloud as needed and when requested by the customer. iViZ follows a hybrid approach for its scan methodology:
- T0 Testing: Automated Testing using multiple in-house and commercial scanners
- T1 Testing: False positives are removed with extensive manual investigation.
- T2 Testing: Business logic verification is carried out with further manual testing using complex attack paths.
The hybrid testing is carried out by combining automation of testing with work flow automation and leveraging process engineering on top of it. In terms of coverage, the service covers OWASP Top 10 and WASC 26 threat classes in premium app testing.
D. Packaging and Pricing
iViZ offers two penetration testing service packages depending on customer business environment – Standard and Premium. Standard Tests are suitable for non critical applications and thus has lesser coverage. Premium is suited for critical applications and thus it provides a deep diagnosis with zero false positive and proof of exploit. The pricing packages are all subscription based with frequency ranging from half yearly, quarterly, yearly and unlimited.
Conclusion
Overall the service looks pretty impressive. It provides a seamless way to do penetration testing on demand without incurring high cost of tools and consultants. Basically, like the sales force of penetration testing. For partners it provides an easy way to deliver penetration testing much more profitably or even set up a security testing business with zero Capex. However, the primary challenge that iViZ faces is sticking to the quality as the volume scales to thousands of scans.
It’s an interesting service and we shall be keeping an eye on it.
nb : darknet
Read More...
![[+]d'ZheNwaY's Blog[+]](http://feeds.feedburner.com/blogspot/YRtWp.1.gif)