We wrote our first review of Acunetix WVS 6 back in January 2009 and published an update about the release of Acunetix Web Vulnerability Scanner (WVS) 6.5 in June 2009.
The team over at Acunetix have been working hard on version 7 for quite some time and released a new build with added features earlier this year in February. It also has an entirely new attack vector, DOM XSS.
If you are already familiar with WVS, it’ll feel on the surface much the same as the old version as the interface hasn’t changed drastically (which is a good thing).
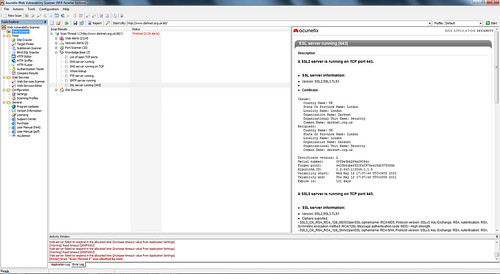
Most of the improvements and major changes in version 7 are under the hood, but at first use you will notice the difference. The scanner is much faster and seems more intelligent (there were noticeably less false positives than I remember in version 6) and it has much better support for Web 2.0 and AJAX powered web applications. That is of course a huge area now and very important for a tool like this that focuses on Web Security to support well (the modules have been re-written to support technologies such as such as JSON, XML and more). It also helps that it uses new unique verification techniques so you don’t have to wade through all the false positives by hand.
The order and layout of the scan results is also clearer and easier to follow with better sections and more information about each alert.
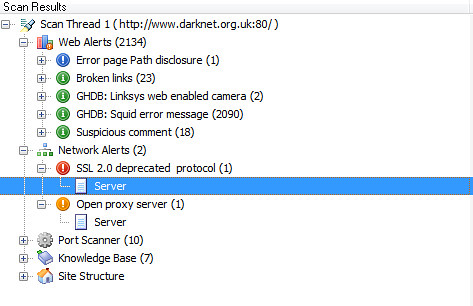
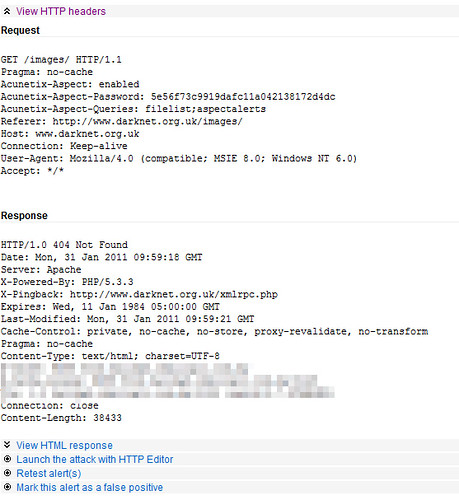
It also gives suggestions on how to fix the issue, these are usually quite general though rather than specific technical instructions. One thing I really like about WVS it’s a very well equipped scanner which can crawl, scan, do vulnerability checks and has a bunch of handy tools for comparing results and even fuzzing.
With the HTTP Fuzzer can define your own character sets, iterations, use files and much more. It’s a very neat tool and not only for fuzzing, you can also use it to validate query sets to create your own valid input rules for WVS to test.
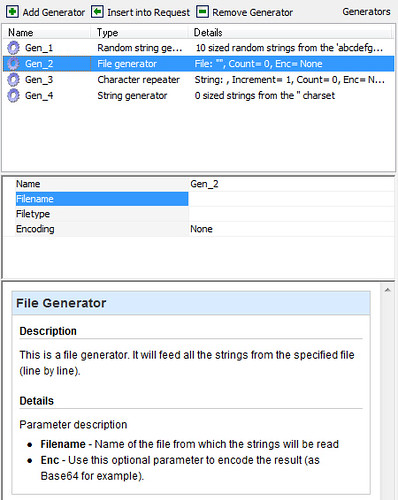
Another useful tool to have built in to this kind of application is a local HTTP Proxy – which is labeled in WVS as HTTP Sniffer. The HTTP Sniffer acts as a proxy and allows you to capture, examine and modify HTTP traffic between an HTTP client and a web server. You can also enable, add or edit traps to trap traffic before it is sent to the web server or back to the web client.
It also has a tool called the Authentication Tester, which you can use to perform dictionary/brute-force attacks against login pages which use both HTTP (NTLM v1, NTLM v2, digest) or form based authentication. This tool uses two predefined text files (dictionaries) which contain a list of common user-names and passwords. You can add your own combinations to these text files. It’s a very easy to setup brute-forcing tool for form-based authentication testing.
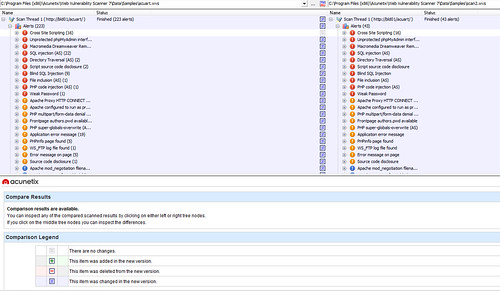
For those of who do this for a living, the Compare Results tool is great for those clients you scan regularly – it even allows you compare site structure. With this and regular scans you can easily monitor if and when any vulnerabilities are introduced and keep things under control.
Overall this new version of WVS feels similar to version 6 but somehow tighter, faster and more efficient – if you liked WVS before, you’ll love it now.
As an addition for the more advanced users, you can actually write your own Acunetix WVS Vulnerability Checks now too. As the new Checks are JavaScript in WVS 7 – it’s faster, easier and more flexible to write completely new Checks or edit existing Checks.
You can get the tool and detailed scripting reference to develop your own Checks here:
Acunetix_SDK.zip
More details about that here:
Creating custom vulnerability checks for Acunetix WVS Version 7
Acunetix WVS Trial Edition
Download Acunetix Web Vulnerability Scanner v7 trial edition from here.
There are also some useful resources here:
nb: darknet
![[+]d'ZheNwaY's Blog[+]](http://feeds.feedburner.com/blogspot/YRtWp.1.gif)

Tidak ada komentar:
Posting Komentar