(For links to all of these downloads in one convenient list, see our "Best Free Software for Protecting Your PC and Your Privacy" collection.)
Protect Against Malware
Malware is the most dangerous threat you'll come across online. Viruses, Trojan horses, and other types of malware can do immeasurable damage to your PC, steal your private information, and even turn your PC into a zombie that spews spam or carries out an attacker's commands. No need to be a victim, though; these freebies will keep you safe.
Microsoft Security Essentials
About as simple to use as protection software gets,
Microsoft Security Essentials sits in the background, scanning the programs you run to determine whether they're malware and then disposing of any that prove to be dangerous. In addition, it regularly scans your system to make sure no infections have gotten through. It's straightforward, clean, and free, a hard combination to beat.
Avast Free Antivirus
This well-designed, speedy antimalware tool is easy to use, and PCWorld rated it as the
top free antivirus program. Like Microsoft's freebie,
Avast Free Antivirus is a set-and-forget utility. Just run it and set the options, and it handles the rest on its own. Its scans are exceptionally fast, and it uses few system resources, so you won't need to spend much time with it. You probably won't even notice that it's running.
Spybot Search & Destroy
This longtime spyware killer is one of the most popular files in PCWorld's Downloads library, and with good reason.
Spybot Search & Destroy, as its name implies, is dedicated to eliminating spyware, and it does a great job. It scans your PC to catch offending spyware, including tracking cookies and spyware apps. It also inoculates your machine against getting infected in the first place.
Comodo Firewall
Every PC needs a good firewall, software that blocks applications on the computer from making unsafe outbound connections. A firewall is especially useful because Trojan horses typically try to make outbound connections; a firewall will also help to prevent your PC from becoming a zombie and doing an attacker's bidding.
Comodo Firewall is a very good choice that blocks Trojan horses, stymies hackers attempting to take control of your PC, and wards off other threats. Note that using it takes a bit of work, since you have to let it know which programs are safe and should be allowed to have outbound connections. But setting that up is a small annoyance in light of the protection Comodo offers.
Stay Safe at Hotspots
When you use a Wi-Fi hotspot at a café, airport, or other public location, your PC and your privacy are particularly vulnerable. In such places it's exceptionally easy for anyone in the area to snoop on your activities as you browse the Web, especially since the advent of the free Firesheep extension that allows anyone without coding experience to steal your Facebook and Twitter identities as well as your logins at other sites. Guard your machine and your data with the following free software.
CyberGhost VPN
The
CyberGhost VPN utility sets up a virtual private network when you connect to the Internet. Simply install and run the software, and hop online. It hides your true IP address and connects you to anonymous servers. In fact, don't feel limited to using it at hotspots--you can also use it whenever you wish to guard your privacy while you surf the Internet.
Note, however, that CyberGhost VPN has a couple of limitations. First, the free version is good for only a 6-hour session or 1GB of downloads; after that, you'll have to restart the session. Second, it typically connects you to servers in Europe, so you may not be able to connect to, say, the U.S. version of Google. If those restrictions are deal-breakers, you could invest in the for-pay service. But if you're spending 6 hours at a time hunkered over your PC in a coffee shop, you may want to rethink your workflow anyway.
HTTPS Everywhere
The free Firefox add-in
HTTPS Everywhere is designed to protect your privacy when you visit specific sites, including Facebook, Google Search, the New York Times, Paypal, Twitter, the Washington Post, and Wikipedia. It's an ideal tool for fending off Firesheep hackers. Note that it protects you only on sites that employ the HTTPS secure protocol, and that it can't help when you're using online services other than Web surfing, such as email and instant messaging. Still, it's a great way to stay safe at certain websites.
Hotspot Shield
This freebie does exactly what its name suggests:
Hotspot Shield protects you when you're connected to a hotspot, by encrypting all of your data packets. When you install it, make sure to decline the extra toolbars. And if you don't want your home page and default search engine to change, uncheck those options as well during installation.
TrackMeNot
Every time you perform a Web search, you give up a bit of your privacy. Search engines track your search terms, and they can build profiles about your interests based on what you search for. The free
TrackMeNot add-in for Firefox and
TrackMeNot add-in for Chrome cleverly thwart such behavior, bombarding search engines with random search terms gleaned from news sites and creating so much "noise" about you that no profile can be created.
Secure Your PC
Finally, you'll want to secure your PC itself--its contents as well as any passwords you've stored on it. The next three freebies will do the work for you.
KeePass
You have plenty of passwords you use every month, for websites, ATMs, email services, and more. Most likely, you've stored them somewhere on your PC--which means that they can be stolen. Lock them away with
KeePass, which hides them in an encrypted database so that only you can use them. In addition, the tool will create industrial-strength passwords for you, making it less likely that anyone will be able to break them.
FreeOTFE
Worried that a snoop can walk by your PC when you're not around, and then access all of its files and applications? Concerned about what might happen to your files and data if you lose your laptop?
FreeOTFE can encrypt files and folders--or your entire hard disk--and then decrypt the data on the fly as you use it. This utility isn't necessarily the easiest program to use, but it does its job nicely.
Secunia PSI
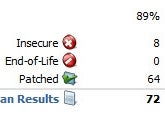
You already know that you should take care of any vulnerabilities in your PC's operating system, but you might be surprised to learn that out-of-date applications can contain security flaws and pose significant problems too. If you have installed applications but neglected to regularly update and patch them, your computer may be at risk.
Secunia PSI closes the holes through which malware can slither. The tool scans the software on your system, determines which programs are outdated, and then helps you install patches.
Read More...
![[+]d'ZheNwaY's Blog[+]](http://feeds.feedburner.com/blogspot/YRtWp.1.gif)






 Assange had shared the passphrase to decrypt the cables with an external source as a protective measure and expected the source to keep the key secret.
Assange had shared the passphrase to decrypt the cables with an external source as a protective measure and expected the source to keep the key secret.