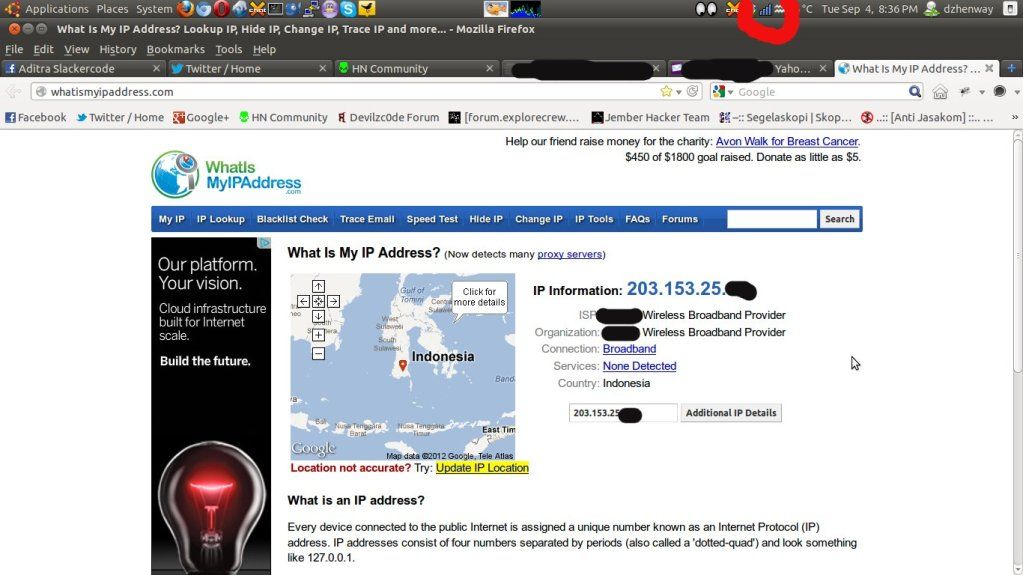
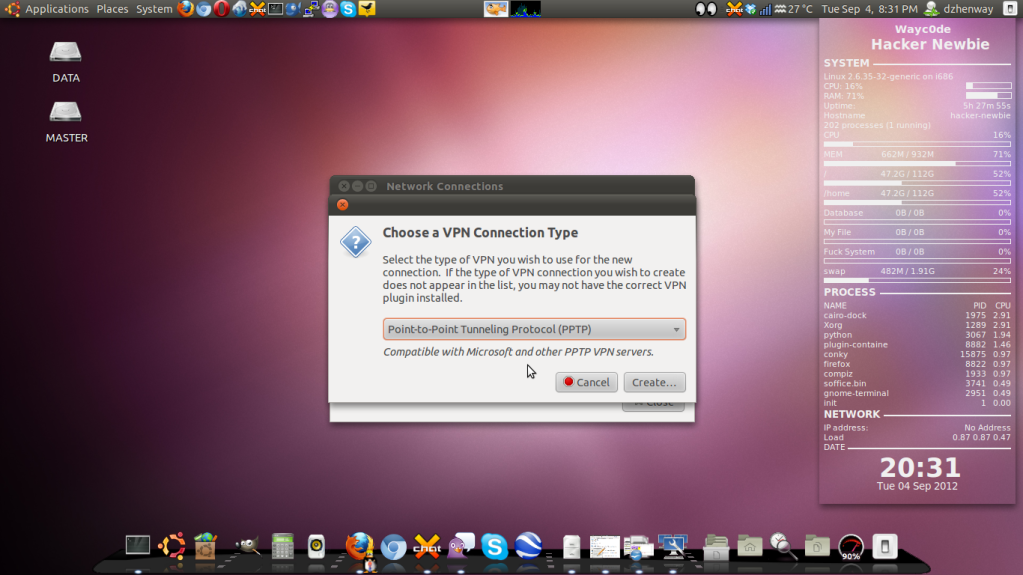
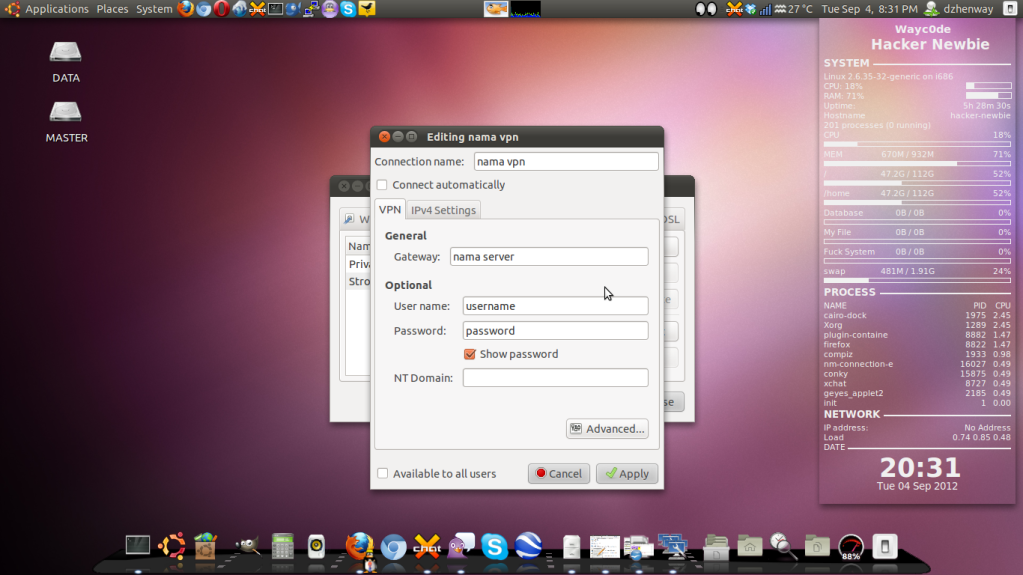
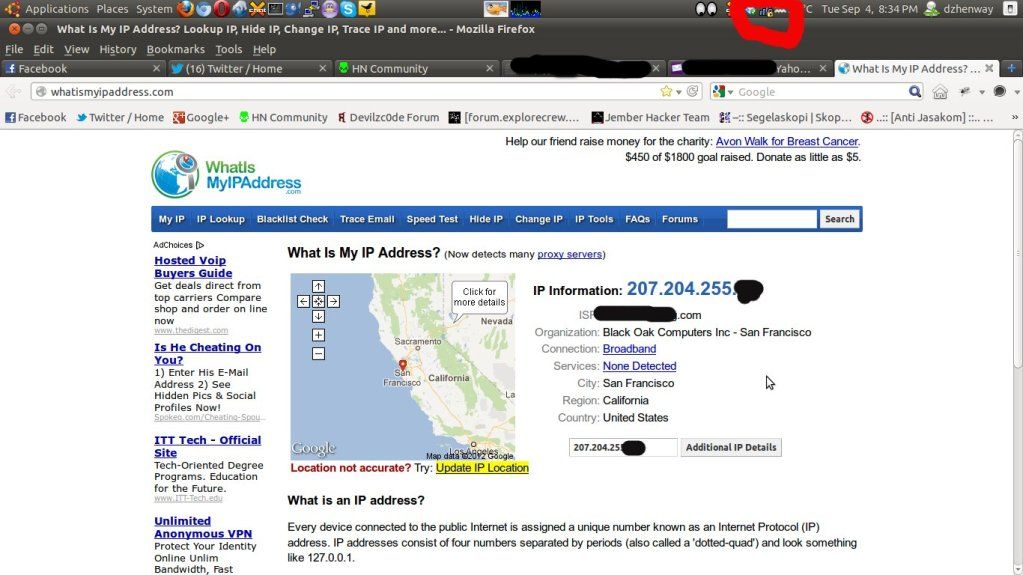
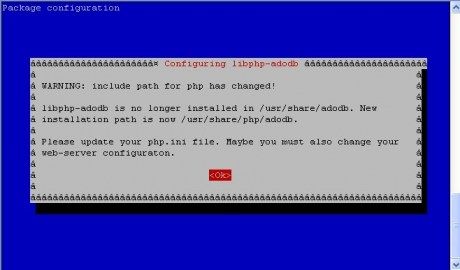
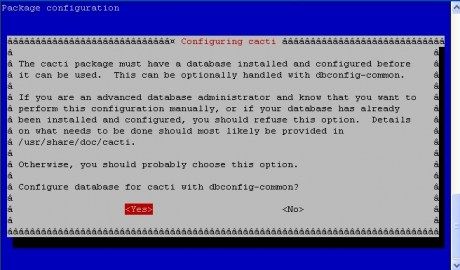
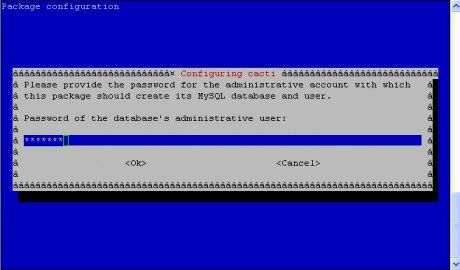
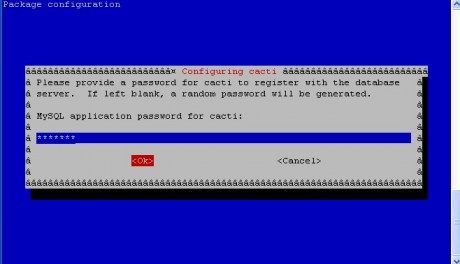
Assalamu'alaikum Wr Wb
sudah lama saya tidak membikin postingan di blog ini, akhirnya hari ini ada niat buat ngisi lagi
CEKIDOT !!!
=============================================================
Anti-Spam
1. ASSP
Replaces: Barracuda Spam and Virus Firewall, SpamHero, Abaca Email Protection Gateway
The self-proclaimed "absolute best SPAM fighting weapon that the world has ever known," ASSP sits on your SMTP servers to stop spam and scan for viruses. Features include browser-based setup, support for most SMTP servers, automatic whitelists, early sender verification, Bayesian filters and more. Operating System: OS Independent.
2. MailScanner
Replaces: Barracuda Spam and Virus Firewall, SpamHero, Abaca Email Protection Gateway
Downloaded more than 1.3 million times by users in 225 countries, MailScanner is a free e-mail security package for mail servers. It incorporates SpamAssassin, ClamAV and a number of other tools to block spam and malware. Operating System: OS Independent.
3. SpamAssasin
Replaces: Barracuda Spam and Virus Firewall, SpamHero, Abaca Email Protection Gateway
"The powerful #1 open-source spam filter," SpamAssassin uses header and text analysis, Bayesian filtering, DNS blocklists, collaborative filtering databases and other techniques to block spam. The project is managed by the Apache Foundation, and it's been incorporated into a number of other open source and commercial products. Operating System: primarily Linux and OS X, although Windows versions are available.
4. SpamBayes
Replaces: Barracuda Spam and Virus Firewall, SpamHero, Abaca Email Protection Gateway
As you might guess from the name, this project offers a group of Bayesian filters for blocking spam. The site includes versions for Outlook, Outlook Express, Windows Live Mail, IncrediMail, Thunderbird, Gmail, Yahoo Mail and others. Operating System: OS Independent.
Anti-Spyware
5. Nixory
Replaces: SpyBot Search and Destroy, AdAware
Nixory removes and block malicious tracking cookies (aka, spyware) from your system. It supports Mozilla Firefox, Internet Explorer and Google Chrome, and it won't slow your system while you surf. Operating System: OS Independent.
Anti-Virus/Anti-Malware
6. ClamAV
Replaces Avast! Linux Edition, VirusScan Enterprise for Linux
This tremendously popular anti-virus engine has been incorporated into numerous security products and calls itself "the de facto standard for mail gateway scanning." The open source version runs on UNIX or Linux mail servers, but the website also offers a version called Immunetfor individual Windows PCs. Operating System: Linux.
7. ClamTK
Replaces Avast! Linux Edition, VirusScan Enterprise for Linux
ClamTK makes ClamAV a little bit easier to use by providing a graphical interface for the anti-virus engine. Like the original, this one runs on Linux and scans on demand. Operating System: Linux.
8. ClamWin Free AntiVirus
Replaces Kaspersky Anti-Virus, McAfee AntiVirus Plus, Norton Anti-Virus
Based on ClamAV, ClamWin protects more than 600,000 PCs from viruses and malware. Note that unlike most commercial anti-virus packages, ClamWin does not offer an on-access real-time scanner; in order to scan incoming files, you'll need to save them and then run a scan manually before opening or running the files. Operating System: Windows.
9. P3Scan
Replaces Avast! Linux Edition, VirusScan Enterprise for Linux
With P3Scan, you can set up a transparent proxy server that provides anti-virus and anti-spam protection. Operating System: Linux.
Backup
10. Amanda
Replaces: Simpana Backup and Recovery , NetVault, HP StorageWorks EBS
Protecting more than 500,000 systems worldwide, Amanda lays claim to the title "most popular open source backup and recovery software in the world." In addition to the community version, it's also available in a supported enterprise edition or as an appliance. Operating System: Windows, Linux, OS X.
11. Areca Backup
Replaces: NovaBackup
Aiming for a balance between simplicity and versatility, Areca offers an easy graphical interface with many options for creating and interacting with archived files. Key features include compression, encryption, delta backup support, archive merges and more. Operating System: Windows, Linux.
12. Bacula
Replaces: Simpana Backup and Recovery , NetVault, HP StorageWorks EBS
Designed for enterprise users, Bacula backs up multiple systems across a network. Commercial support and services for the popular product are available through Bacula Systems. Operating System: Windows, Linux, OS X.
13. CloneZilla
Replaces: Norton Ghost
Created as an alternative to Ghost, Clonezilla can clone single or multiple systems very quickly. It comes in two versions: Clonezilla Live for individual systems and Clonezilla SE for massive networks. Operating System: Windows, Linux, OS X.
14. PartiMage
Replaces: Norton Ghost, NovaBackup, McAfee Online Backup, Carbonite.com
Partimage can create a complete image of your system, which is useful if you need to recover from a full system crash or if you want to configure multiple systems with exactly the same software. It can also create a recovery partition on your drive. Operating System: Linux.
15. Redo
Replaces: Norton Ghost, NovaBackup, McAfee Online Backup, Carbonite.com
Calling itself the "easiest, most complete disaster recovery solution available," Redo offers backup, restore and bare-metal recovery capabilities. Even in the most severe emergencies where you must completely replace a drive, Redo claims it can get you back up and running with all of your programs and files in just 10 minutes. Operating System: Linux.
Browsers
16. Chromium
Replaces: Microsoft Internet Explorer
The open source version of Google Chrome, Chromium tends to be faster and more secure than competing browsers. Key security features include sandboxing, automatic updates, SafeBrowsing and more. Operating System: Windows, Linux, OS X.
17. Dooble
Replaces: Microsoft Internet Explorer
Dooble's developers have created this newer browser with an eye on safety and ease of use. Unlike most other browsers, it automatically encrypts all traffic for greater privacy and security. Operating System: Windows, Linux, OS X.
18. Tor
Replaces: Microsoft Internet Explorer
Tor protects your identity by providing anonymity while you browse the Web. It's used by journalists, activists, whistle-blowers and others concerned that someone might be snooping on their online activities. Operating System: Windows, Linux, OS X.
Browser Add-Ons
19. Web Of Trust
Replaces: McAfee SiteAdvisor Plus
Downloaded more than 33 million times, this popular add-on for Firefox, Internet Explorer, Chrome, Safari or Opera lets users know when they've strayed into websites that are questionable or insecure. It utilizes user ratings to identify sites that perpetuate scams, collect personal information or include unsuitable content, and it ranks them with a green-yellow-red classification system. Operating System: Windows, Linux, OS X.
20. Password Maker
Replaces Kaspersky Password Manager, Roboform
Using the same password all the time puts you at risk, but many people do it anyways because it's so difficult to remember a lot of different passwords. This browser add-on offers a better solution for the problem by creating unique passwords for each site you visit and storing them in an encrypted file that you access with a single master password. Operating System: Windows, Linux, OS X.
Data Removal
21. BleachBit
Replaces Easy System Cleaner
This helpful utility cleans up your system to protect your privacy and improve performance. It frees up disk space by cleaning junk from more than 90 applications, erasing temporary files, deleting cache and browsing history, and "shredding" unwanted files. Operating System: Windows, Linux.
22. Eraser
Replaces BCWipe Enterprise
Like BleachBit, Eraser "shreds" deleted files so that they cannot be recovered. It helps protect sensitive information by rewriting over deleted files several times with random data. Operating System: Windows
23. Wipe
Replaces BCWipe Enterprise
Wipe offers the same functionality as Eraser, but it's for Linux instead of Windows. The site also offers a wealth of information for those interested in learning more about how file "shredding" works. Operating System: Linux.
24. Darik's Boot And Nuke
Replaces Kill Disk, BCWipe Total WipeOut
While Eraser and Wipe delete single files, DBAN securely deletes entire disks. It's very helpful when donating or disposing of an old system. Operating System: OS Independent.
Data Loss Prevention
25. OpenDLP
Replaces RSA Data Loss Prevention Suite, CheckPoint DLP Software Blade, Symantec Data Loss Prevention Product Family
OpenDLP is a "agent- and agentless-based, centrally-managed, massively distributable data loss prevention tool." It allows security or compliance managers to scan thousands of systems simultaneously via agents or perform agentless data discovery against a MySQL or Microsoft SQL server. Operating System: Windows.
26. MyDLP
Replaces RSA Data Loss Prevention Suite, CheckPoint DLP Software Blade, Symantec Data Loss Prevention Product Family
MyDLP can block credit card numbers, social security numbers, or sensitive files from being transmitted via e-mail, printers, the Web or removable devices. In addition to the free community version, it also comes in a paid enterprise version. Operating System: Windows, Linux, VMware.
Encryption
27. AxCrypt
Replaces McAfee Anti-Theft, CryptoForge
With nearly 2.5 million registered users, AxCrypt claims to be the "leading open source file encryption software for Windows." It integrates with Windows Explorer—to use it, you simply right-click to encrypt a file or double-click to decrypt. Operating System: Windows.
28. Gnu Privacy Guard
Replaces PGP Universal Gateway Email Encryption
This Gnu project is a command-line implementation of the popular OpenPGP encryption standard. It supports ElGamal, DSA, RSA, AES, 3DES, Blowfish, Twofish, CAST5, MD5, SHA-1, RIPE-MD-160 and TIGER encryption algorithms. Operating System: Linux.
29. GPG Tools
Replaces PGP Universal Gateway Email Encryption
Mac users can download this version of GPG for a more user-friendly way to encrypt e-mail and files. The website includes quite a bit of help and tutorials for new users, which make it even easier to get started using the app. Operating System: OS X.
30. GPG 4 Win
Replaces Cypherus
And this version offers GPG for Windows users, complete with a GUI. It installs quickly and easily, and it protects both files at rest and mail messages. Operating System: Windows.
31. PeaZip
Replaces WinZip
While it's really a compression utility not an encryption tool, PeaZip also offers strong encryption capabilities, which is why we included it in this section of the list. It also includes two-factor authentication capabilities and secure deletion. Operating System: Windows, Linux.
32. Crypt
Replaces McAfee Anti-Theft, CryptoForge
At just 44KB, Crypt is one of the lightest weight encryption utilities available. And because it can encrypt 3MB worth of data in just 0.7 seconds, it's also one of the fastest. However, it doesn't have a GUI, so you'll need to be comfortable with the command line in order to use it. Operating System: Windows.
33. NeoCrypt
Replaces McAfee Anti-Theft, CryptoForge
NeoCrypt supports multiple encryption algorithms, including AES, DES, Triple-DES, IDEA, RC4, RC5, CAST-128, BlowFish, SkipJack. It runs from an easy-to-use GUI, and it also integrates with the Windows Shell so that you can encrypt and decrypt files right from Windows Explorer. Operating System: Windows.
34. LUKS/CyrptSetup
Replaces PGP Whole Disk Encryption
Short for "Linux Unified Key Setup," LUKS calls itself "the standard for Linux hard disk encryption." While many of the other apps on our list encrypt files one by one, LUKS encrypts your entire drive. Operating System: Linux.
35. FreeOTFE
Replaces PGP Whole Disk Encryption
Like LUKS, this app encrypts an entire drive. With it you can create and encrypt virtual disks on your hard drive. It's also highly portable and can run from a thumb drive. Operating System: Windows.
36. TrueCrypt
Replaces PGP Whole Disk Encryption
One of the most popular open source disk encryption options, TrueCrypt boasts more than 22 million downloads. Thanks to parallelization and pipelining technology, it offers fast reads and writes 0f encrypted information. Operating System: Windows.
Secure File Transfer
37. WinSCP
Replaces CuteFTP, FTP Commander
Extremely popular, the award-winning WinSCP includes an SFTP client, SCP client, FTPS client and FTP client. It offers two different interfaces and also includes an integrated text editor. Operating System: Windows.
38. FileZilla
Replaces CuteFTP, FTP Commander
While WinSCP offers only a client version, FileZilla offers both a client version and a version that allows you to set up your own FTP server. It supports FTP, FTPS and SSH transfer protocol. Operating System: Windows, Linux, OS X.
Forensics
39. Odessa
Replaces EnCase Forensics, X-ways Forensics, AccessData Forensic Toolkit
The Open Digital Evidence Search and Seizure Architecture, aka "ODESSA," offers several different tools that for examining and reporting on digital evidence. This is an older project, but still valuable. Operating System: Windows, Linux, OS X.
40. The Sleuth Kit/AutoPsy Browser
Replaces EnCase Forensics, X-ways Forensics, AccessData Forensic Toolkit
These two apps work together: The Sleuth Kit offers command line tools for conducting digital investigations, and Autopsy Browser offers a browser-based GUI for accessing those tools. The project also now includes a Hadoop framework for large-scale data analysis. Operating System: Windows, Linux, OS X.
Gateway/Unified Threat Management Appliances
41. Endian Firewall Community
Replaces: Check Point Security Gateways, SonicWall, Symantec Web Gateway
Endian Firewall Community can turn any PC (including pretty old ones) into a gateway security appliance complete with a firewall, application-level proxies with antivirus support, virus and spam-filtering for email, Web content and a VPN. Supported versions of the software and hardware appliances are also available on the site. Operating System: Linux.
42. Untangle Lite
Replaces: Check Point Security Gateways, SonicWall, Symantec Web Gateway
Similar to Endian, Untangle Lite also helps users create their own gateway security appliances. In addition, Untangle offers commercial products, and you can download each of the individual apps included in Untangle Lite (firewall, intrusion prevention, attack blocker, etc.) separately. Operating System: Linux.
43. ClearOS
Replaces: Check Point Security Gateways, SonicWall, Symantec Web Gateway
ClearOS combines gateway security functionality with the capabilities of a small business server. It offers networking, groupware, a mail server, a Web server and more. Paid support and hardware are also available. Operating System: Linux.
Intrusion Detection
44. Open Source Tripwire
Replaces Tripwire
Standard Tripwire is now a closed source project, but the community has continued developing the open source version released in 2000. It monitors the content of files and alerts network managers when those files have changed, alerting them to possible intrusions. Operating System: Windows, Linux.
45. OSSEC
Replaces Corero IPS, < ahref="http://www.hpenterprisesecurity.com/products/hp-tippingpoint-network-security/">HP Tipping Point IPS, Sophos HIPS
In addition to file integrity checking, OSSEC also performs log analysis, policy monitoring, rootkit detection and real-time alerting to help prevent and detect intrusions into your network. It's downloaded more than 5,000 times per month and has won numerous awards. Operating System: Windows, Linux.
46. AFICK
Replaces Tripwire
AFICK, short for "Another File Integrity Checker," offers similar functionality as Tripwire. It's portable, fast and runs from a GUI or the command line. Operating System: Windows, Linux.
47. Snort
Replaces Corero IPS, < ahref="http://www.hpenterprisesecurity.com/products/hp-tippingpoint-network-security/">HP Tipping Point IPS, Sophos HIPS
With millions of downloads and more than 400,000 registered users, Snort claims to be "the most widely deployed IDS/IPS technology worldwide." Operating System: Windows, Linux OS X.
Network Firewalls
48. IPCop
Replaces Barricuda NG Firewall, Check Point Appliances
Like most of the other apps on our Firewall list, IPCop turns a PC into a Linux-based firewall to protect your network. This one is designed for home or SOHO users, and it boasts an easy-to-use Web interface. Operating System: Linux.
49. Devil-Linux
Replaces Barricuda NG Firewall, Check Point Appliances
Although it was originally designed to offer firewall and router functionality, Devil-Linux can also operate as a server for many applications, including mail hosting. Created by IT administrators for IT administrators, it boasts top-notch security and excellent customization capabilities. Operating System: Linux.
50. Turtle FireWall
Replaces Barricuda NG Firewall, Check Point Appliances
Designed to be simple and fast, Turtle allows network managers to configure it via a Web interface or by modifying XML files. The website also includes some good introductory information on the nature of firewalls. Operating System: Linux.
51. ShoreWall
Replaces Barricuda NG Firewall, Check Point Appliances
Shorewall doesn't claim to be the easiest Linux firewall to use, but it does claim to be "the most flexible and powerful." You can use it on a system functioning as a dedicated firewall, as a multi-function gateway/router/server or as a standalone GNU/Linux PC. Operating System: Linux.
Network Firewalls (continued from previous page)
52. Vuurmuur
Replaces Barricuda NG Firewall, Check Point Appliances
Vuurmuur is designed to be both simple and powerful. In addition to standard firewall capabilities, it also supports traffic shaping and offers advanced monitoring capabilities. Operating System: Linux.
53. M0n0wall
Replaces Barricuda NG Firewall
Although it was designed for embedded PCs and appliance, m0n0wall can also run on a standalone PC running FreeBSD. It requires less than 12MB of space and boots in less than 25 seconds. Operating System: FreeBSD.
54. pfSense
Replaces Barricuda NG Firewall, Check Point Appliances
This m0n0wall fork is also based on BSD, but is designed for regular computers, not embedded hardware. It's been downloaded more than 1 million times and currently runs on more than 100,000 networks, including large corporations and universities as well as small home networks. Operating System: FreeBSD.
55. Vyatta
Replaces Cisco products
The "core" Vyatta software allows users to make their own firewalls/networking appliances and routers. The company also offers paid software and hardware. Operating System: Linux.
Network Monitoring
56. Wireshark
Replaces: OmniPeek, CommView
Calling itself the "world's foremost network protocol analyzer," Wireshark makes it easy to capture and analyze network traffic. Commercial products and services related to the software are available through Riverbed Technology. Operating System: Windows, Linux, OS X.
57. TcpDump/Libpcap
Replaces: OmniPeek, CommView,
Tcpdump is a command line packet analyzer, and libpcap is a C/C++ library for network traffic capture. Working together, the two provide a good network monitoring solution, but, lacking a GUI, they are not particularly user-friendly. Operating System: Linux.
58. WinDump
Replaces: OmniPeek, CommView
Managed by Riverbed Technology (which also owns Wireshark), WinDump ports tcpdump to the Windows platform. This site also includes the WinPcap library and drivers for traffic capture. Operating System: Windows.
Password Crackers
59. OphCrack
Replaces Access Data Password Recovery Toolkit, Passware
From time to time, everyone needs to recover a lost or unknown password. This password cracker uses the rainbow tables method to recover unknown passwords, and it also includes a brute force module for simple passwords. Operating System: Windows.
60. Access Data Password Recovery, Passware
John the Ripper is particularly good at cracking weak passwords, but in order to use it, you'll need a list of commonly used passwords. You can buy password lists or a pro version of the software from the same site. Operating System: Windows, Linux, OS X.
Password Management
61. KeePass Password Safe
Replaces Kaspersky Password Manager
This popular password manager stores all of your passwords in an encrypted database. You'll only need to remember one master password, while this easy-to-use, lightweight app helps protect you from identity thieves. Operating System: Windows.
62. KeePassX
Replaces Kaspersky Password Manager
If you use OS X or Linux, try this fork of KeePass. Plus, it adds a few features not in the original and runs on Windows as well. Operating System: Windows, Linux, OS X.
63. Password Safe
Replaces Kaspersky Password Manager
Downloaded more than 1 million times, Password Safe is another popular open source option for protecting your passwords. Like KeePass, it's lightweight and stores your encrypted passwords in a database so that you only need to recall one master password. Operating System: Windows.
User Authentication
64. WIKID
Replaces Entrust IdentityGuard, Vasco Digipass, RSA's SecurID
WiKID boasts "two-factor authentication without the hassle factor." In addition to the free community version, it also comes in a supported enterprise version which also adds additional functionality. Operating System: OS Independent.
Web Filtering
65. DansGuardian
Replaces McAfee Family Protection
NetNanny, CyberPatrol
This award-winning content filter uses phrase matching, PICS filtering, URL filtering and other methods to block objectionable content. Note that this software does not run on individual PCs; it runs on an OS X or Linux server to protect the rest of your network. Operating System: Linux, OS X.
=============================================================
mungkin sekian dulu dari ane, semoga bermanfaat bagi kita semua
wassalamu'alaikum wr wb
Sumber
Read More...
![[+]d'ZheNwaY's Blog[+]](http://feeds.feedburner.com/blogspot/YRtWp.1.gif)