Criminals who operate large groupings of hacked PCs tend to be a secretive lot, and jealously guard their assets against hijacking by other crooks. But one of the world’s largest and most sophisticated botnets is openly renting its infected PCs to any and all comers, and has even created a Firefox add-on to assist customers.
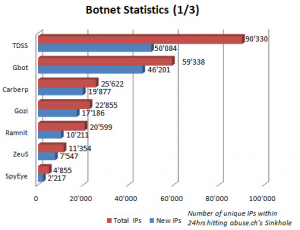
The TDSS botnet is the most sophisticated threat today, according to experts at Russian security firm Kaspersky Lab. First launched in 2008, TDSS is now in its fourth major version (also known as TDL-4).
The malware uses a “rootkit” to install itself deep within infected PCs, ensuring that it loads before the Microsoft Windows operating system starts. TDSS also removes approximately 20 malicious programs from host PCs, preventing systems from communicating with other bot families.
In an exhaustive analysis of TDSS published in June, Kaspersky researchers Sergey Golovanov and Igor Soumenkov wrote that among the many components installed by TDSS is a file called “socks.dll,” which allows infected PCs to be used by others to surf the Web anonymously.
The storefront for this massive botnet is awmproxy.net, which advertises “the fastest anonymous proxies.” According to Golovanov, when socks.dll is installed on a TDSS-infected computer, it notifies awmproxy.net that a new proxy is available for rent. Soon after that notification is completed, the infected PC starts to accept approximately 10 proxy requests each minute, he said.
“For us it was enough to see that this additional proxy module for tdl4 was installed directly on encrypted partition and runs thru rootkit functionality,” Golovanov told KrebsOnSecurity. “So we believe that awmproxy has direct connection to tdl4 developer but how they are working together we don’t know.” The curators of AWMproxy did not respond to requests for comment.
The service’s proxies are priced according to exclusivity and length of use. Regular browser proxies range from $3 per day to $25 monthly. Proxies that can be used to anonymize all of the Internet traffic on a customer’s PC cost between $65 and $500 a month. For $160 a week, customers can rent exclusive access to 100 TDSS-infected systems at once. Interestingly, AWMproxy says it accepts payment via PayPal, MasterCard, and Visa.
Awmproxy.net currently advertises more than 24,000 proxies for rent. The number of available proxies varies greatly from day to day, even within a single 24-hour period. That’s because the TDSS-infected systems aren’t always turned on: Their legitimate, oblivious owners sometimes turn their PCs off at night and on weekends.
This is explained in AWMproxy’s FAQ:
“Q: Today quality/speed/number of proxies decreased, can you do something?The renting of hacked PCs for anonymous surfing is only one of the many ways the TDSS authors monetize their botnet. In a blog post published today, Golovanov discusses how TDSS is being used for mining Bitcoins, an electronic currency.
A: There are time periods when the proxies quality, number and speed decrease, and we are really unable to help it much as we would like to. It is impossible to provide the same number of proxies in the day time and at 3 a.m. The same is true for weekends.”
“What I think they’re doing is renting to these sites the ability to have people visit them so they can get paid for display ads,” Mlodzianowski said. “A campaign file is a list of about 15 sites. The [bots] don’t hit just one page, they crawl through and visit two to three pages on each site, so it looks like a real user is doing that. All of this happens so that it is invisible to the user.”
It’s not clear yet whether the fraudsters running the TDSS botnet operate a similar public storefront for click fraud clients. But it’s remarkable that those responsible for TDSS feel so invulnerable that they are comfortable advertising their work in such a public fashion.
nb : krebsonsecurity
![[+]d'ZheNwaY's Blog[+]](http://feeds.feedburner.com/blogspot/YRtWp.1.gif)

Tidak ada komentar:
Posting Komentar